La signature électronique sans limites.
Pour tous les usages et tous les métiers
Depuis 2005, la confiance règne.
Pourquoi adopter la signature électronique ?
Instrument essentiel pour lutter contre la fraude et améliorer votre productivité, la signature électronique permet, notamment grâce au règlement eIDAS, d’offrir un niveau de signature légal à vos documents dématérialisés.
Sécurisez vos accords
La signature électronique garantit l’intégrité de vos contrats, permettant ainsi de prouver qu’ils n’ont pas été retouchés.
Fiabilisez vos parcours contractuels
La signature électronique assure l’identité des contractants et l’authenticité des documents.
Accélérez la signature de vos contrats
Signez où vous voulez, en quelques clics.
Gagnez en productivité
Finis les aller-retours à la photocopieuse. Dites adieu aux documents à signer oubliés au coin d’un bureau. Libérez du temps pour les tâches essentielles.
Réduisez vos coûts
Mécaniquement, les gains en productivité se traduisent en baisse des coûts de fonctionnement. Pour les grandes organisations, les économies d’impression, d’affranchissement, et de déplacement peuvent être considérables.
Gagnez en praticité
Facilitez l’archivage des documents et simplifiez l’accès aux dossiers de preuves pour une consultation à n’importe quel instant.

Sécurisez vos accords
La signature électronique garantit l’intégrité de vos contrats, permettant ainsi de prouver qu’ils n’ont pas été retouchés

Fiabilisez vos parcours contractuels
La signature électronique assure l’identité des contractants et l’authenticité des documents.

Accélérez la signature de vos contrats
La signature électronique assure l’identité des contractants et l’authenticité des documents.

Gagnez en productivité
Finis les aller-retours à la photocopieuse. Dîtes adieu aux documents à signer oubliés au coin d’un bureau. Libérez du temps pour les tâches essentielles.

Réduisez vos coûts
Mécaniquement, les gains en productivité se traduisent en baisse des coûts de fonctionnement. Pour les grandes organisations, les économies d’impression, d’affranchissement, et de déplacement peuvent être considérables.

Gagnez en praticité
Facilitez l’archivage des documents et simplifiez l’accès aux dossiers de preuves pour une consultation à n’importe quel instant.
Des atouts qui font la
différence.
Sécurité
- HDS
- CSPN ANSSI
- ISO 27001
- Datacenters en France
Productivité
- Intégrations à vos applications métier
- SLA 99,9%
- Documents en masse, tous volumes
Simplicité
- Ordinateur, tablette, mobile
- Déploiement et prise en main rapides
- Convient à tous vos cas d’usage
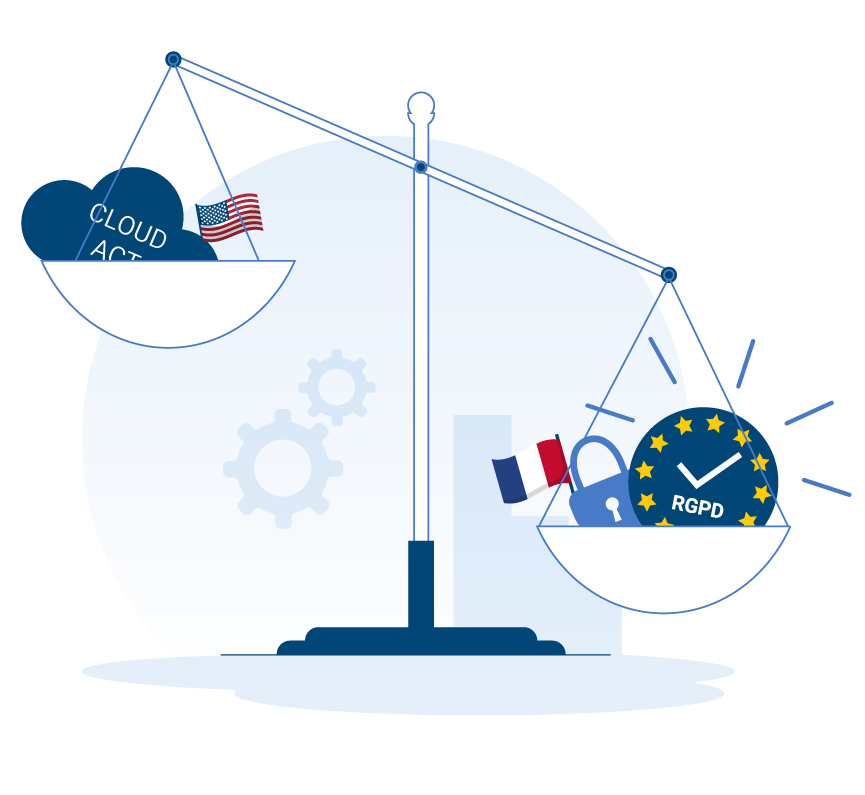
Vos données restent
vos données.
Données souveraines…
Les documents ne sortent pas de votre infrastructure si vous êtes en mode OnPrem, ils ne sortent pas de notre infrastructure si vous êtes en mode Saas. Dans les deux cas vous conservez la même valeur probatoire.
…et hébergées en France
Société de droit français, conforme au RGPD, toutes les données qui transitent par nos serveurs sont hébergées en France. Nous ne sommes pas soumis au Cloud Act*.
* Promulgué en 2018 par Donald Trump, le Cloud Act permet aux USA de consulter les données hébergées dans les serveurs d’autres pays, au nom de la protection et de la sécurité des États-Unis.
Entre de bonnes mains.
Afin de garantir des échanges hautement sécurisés, nous exigeons le meilleur.
Vous désirez intégrer une de nos solutions, ou simplement vous renseigner ?
Nos experts sont là pour vous répondre.